Artwork: Panopticities
Title: Panopticities
Type: Video Installation
Production year: 2018
Running time: looped videos
Dimensions: variable
by KairUs Art+Research (Linda Kronman, Andreas Zingerle)
Locations: Seoul (Republic of Korea), Tokyo (Japan), Bangalore (India), New York City (USA)
Voices:
Seoul: 松村淳子 Atsuko Matsumura, 鈴木啓二朗 Keijiro Suzuki, 近藤令子 Reiko Kondo, 長谷部勇人 Yuto Hasebe. Sound recording: 長谷部勇人 Yuto Hasebe.
Bangalore: robinjoseph23, pragyajha937
New York City: Mark Baldridge
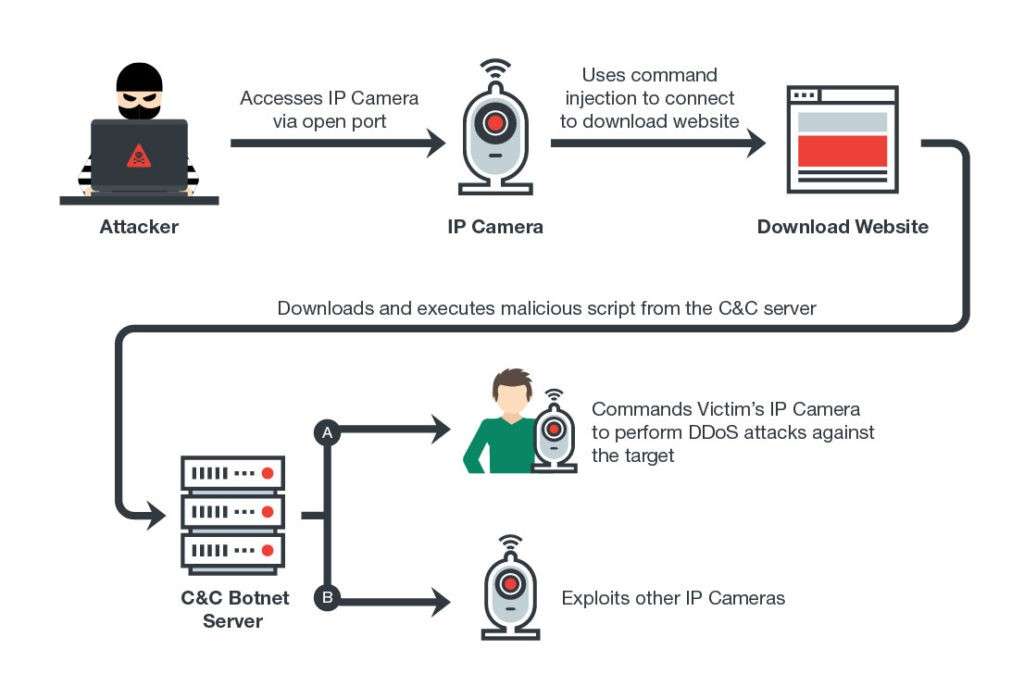
The video portrays mega-cities through the lenses of unsecured public CCTV and private IP cameras. Networked security cameras offer 24/7 surveillance. Tracking software and the integrated web-server allow processing and streaming as part of the growing amount of connected devices also known as the Internet of Things. These web-servers are often insecure by design, meaning they are not protected by a password or have hard-coded login credentials saved as plain text. By default, the servers stream unencrypted and on publicly-accessible network ports, providing potential risks of being intercepted and allowing unknown third parties unintended access to the set up function of the cameras. Some manufacturers use the same vulnerable settings across their entire camera lineup. “By default, the Network Camera is not password-protected”, or “the default user name is admin” and “the password is 12345” can be read in the camera manuals. Security cameras are supposed to offer security, not provide surveillance footage for anyone to view. Often, camera owners don’t realize that their cameras are accessible on the Internet with default insecure settings, enabling hackers to enslave these cameras into botnets. Malware will use insecure webcams to infect the rest of the network, routers and other devices in the “smart home”, threatening both the reliability of surveillance cameras and also serving as a transmission vector to attack other devices.
Surveillance cameras infected with malicious code / enslaved in Botnets: (Source: Trendmicro)
Screenshot:



Video: The installation consists of several videos that are arranged individually depending on room dimension, projection and screen size.
Exhibitions:
June 2018: Artistic Reconnaisance, CICA museum, Gimpo-si, (Republic of Korea)

